Security Predicates in Tableau CRM(Einstein Analytics) : jayakrishnasfdc
by: jayakrishnasfdc
blow post content copied from Jayakrishna Ganjikunta
click here to view original post
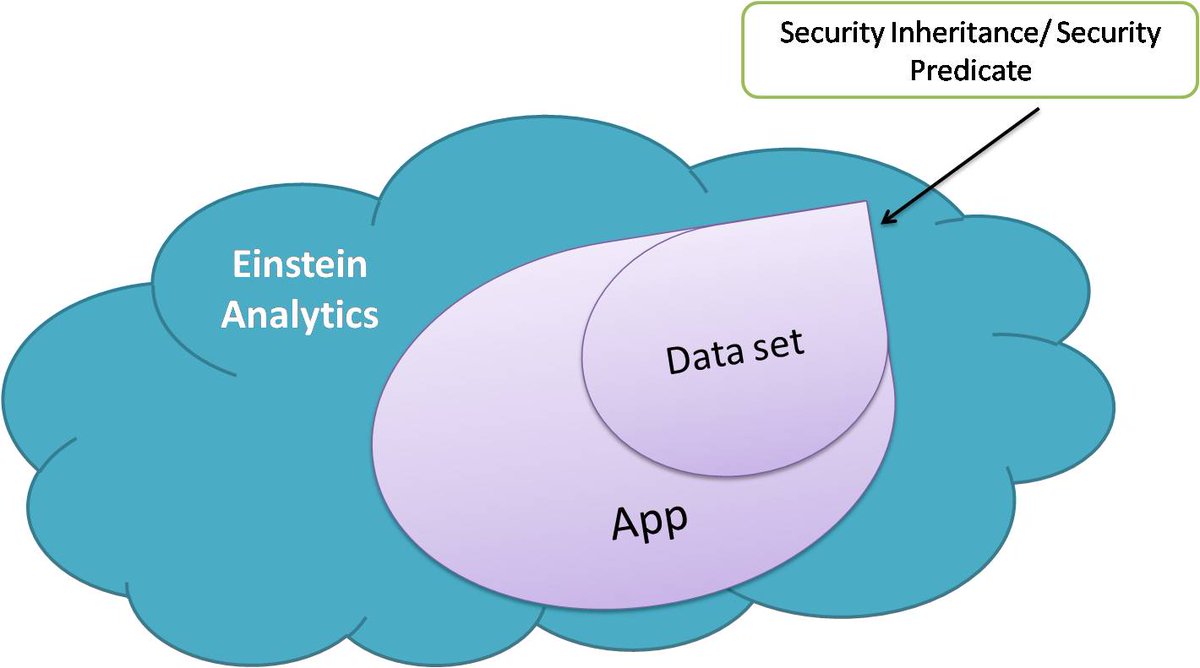
Analytics has different levels of security that your organization can implement to ensure that the right user has access to the right data. Analytics supports security predicates, a robust row-level security feature that enables you to model many different
types of access controls on datasets. Also, Analytics supports sharing inheritance, to synchronize with sharing that’s configured
in Salesforce, subject to certain limitations. If you use sharing inheritance, you must also set a security predicate to take over
in situations when sharing settings can’t be honored.
If a Tableau CRM user has access to a dataset, the user has access to all records in the dataset by default. To restrict access to records, you can implement row-level security on a dataset when you use sharing inheritance and security predicates. Sharing inheritance automatically applies a Salesforce object’s sharing logic to the dataset’s rows. A security predicate is a manually assigned filter condition that defines dataset row access.
To implement effective dataset row-level security, most Salesforce orgs can use a combination of sharing inheritance and a backup security predicate. Sharing inheritance provides the correct record access to your users who do not have many employees or shared records. For users with access to many of their own or shared records, like a CEO or dashboard builder, a security predicate is set as backup to sharing inheritance.
In Einstein Analytics we can Achieve Security by below 4 ways…
1. Using Security Predicates
2. EA Application and Dashboard level Access Implementation
3. EA Access Permissions
4.Salesforce Sharing Inheritance
Using Security Predicates
When a new dataset is created, the security predicate is empty, which means everyone has access to the dataset, has access to all the data rows. Security predicate is a manually assigned filter condition that defines row level security for dataset. When a user submits a query against a dataset that has a predicate, Analytics checks the predicate to determine which records the user has access to. If the user doesn’t have access to a record, Analytics does not return that record.
Types of Security Predicate
- Record ownership – Enables each user to view only records that they own.
- Management visibility – Enables each user to view records owned or shared by their subordinates based on a role hierarchy.
- Team or account collaboration – Enables all members of a team, like an opportunity team, to view records shared with the team.
- Combination of different security requirements – Defines a predicate based on the Salesforce role hierarchy, teams, and record ownership.
The predicates can be formulated to control the data visibility based on the following scenarios:
- Role Hierarchy: Security Predicates can apply row level filter on the data based on the logged in user’s role in the Salesforce org. A user would have visibility to records that they own and the records owned by people below their role hierarchy in the org.
- Manager Hierarchy: Security Predicates can be applied to filter data based on the Manager field in the User object in Salesforce org. In this scenario, the logged-in user would be able to view the records that they own and the records owned by user who report to them in the manager hierarchy (record owner’s manager, record owner’s manager’s manager, etc.)
- Logged in User’s Country: Security Predicate can filter the data based on the logged in user’s country. For example, records that are owned by users from Germany can be made visible only to user’s from that country.
- Opportunity Team and Accounts Team: Security Predicates can be used to filter data visibility based on the condition that the logged-in user is part of the Opportunity Team or Account Team of the record owner. This scenario is applicable only if the Opportunity Team and Account Team features are used in the respective Salesforce org.
- User Territory : Security Predicates can be used to implement Row Level Security based on User Territory. If the Territory Management is used in the respective Salesforce Org.
Syntax:
Predicate Expression Syntax for Datasets You must use valid syntax when defining the predicate expression.
The predicate expression must have the following syntax:
<dataset column> <operator> <value>
For example, you can define the following predicate expression for a dataset:
‘UserId’ == “$User.Id”
- UserId is the API name of the dataset
- == is the operator
- $User.Id this is the current Salesforce User Id when open the dashboard or lens
You can create more complex predicate expressions such as:
(‘Expected_Revenue’ > 4000 || ‘Stage Name’ == “Closed Won”) && ‘isDeleted’ != “False”
Consider the following requirements for the predicate expression:
• The expression is case-sensitive.
• The expression cannot exceed 5,000 characters.
• There must be at least one space between the dataset column and the operator, between the operator and the value, and before and after logical operators. This expression is not valid: ‘Revenue’>100. It must have spaces like this: ‘Revenue’ > 100. If you try to apply a predicate to a dataset and the predicate is not valid, an error appears when any user tries to query the dataset
Sample Example:
Login to Salesforce Einstein Org. Navigate to App Launcher –> Einstein Studio –> Datasets.

Click on Edit and it will open the Dataset in a new tab. If you observe, right now there is no security predicate defined for this dataset.

Now, we will define the security predicate to restrict records. User will have access to his/her own records along with that owned by it’s subordinate. Click on the edit option below Security Predicate at bottom of the screen.

Once security predicate is applied, user can only access the data he/she is entitled to.
Thanks
Jayakrishna
February 20, 2021 at 04:23PM
Click here for more details...
=============================
The original post is available in Jayakrishna Ganjikunta by jayakrishnasfdc
this post has been published as it is through automation. Automation script brings all the top bloggers post under a single umbrella.
The purpose of this blog, Follow the top Salesforce bloggers and collect all blogs in a single place through automation.
============================

Post a Comment